Configuring Active Directory as Identity Source for use with SSO 6.0 can be done in 2 ways
a. Use the Machine Account(Any AD Account)
b. Use with Service Principal Name
The below is the step-by-step procedure for configuring via Service Principal Name
Prerequisite:
1. A domain account with domain administrator privileges is required when assigning a SPN to an account.
2. A domain account with domain user privileges is a minimum requirement for the account to be used as the SPN account.
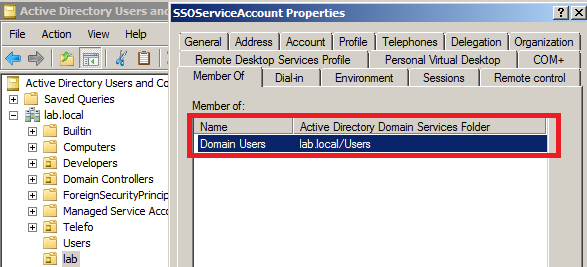
3. You need access to vCenter Server running on a Windows platform or a Windows system connected to the same domain as vCenter Server Appliance.
Creating an SPN for use with SSO 6.0 :
Validation :
To verify that an SPN does not already exist on the account to be used:
Type the following command to verify that no other SPNs have been created on this domain for
setspn -Q sts/DNS_domain_name
For example:
C:\>setspn -Q STS/lab.local
You see output similar to:
No such SPN Found.
1. Log in to vCenter Server using a domain administrator account.
Note: If using the vCenter Server Appliance 5.1 (VCSA), these actions can be performed on a Windows workstation joined to the same domain as the VCSA.
2. Open an elevated command prompt. For more information, see Opening a command or shell prompt
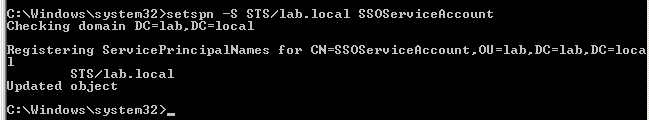
3. Type the following command and press enter
setspn -S sts/DNS_Domain_name Domain_User_account
For example:
C:\>setspn -S STS/lab.local SSOServiceAccount
You see output similar to:
Notes:
If a duplicate SPN is found, check your Active Directory administrator for deleting the SPN.
You must use the SPN name STS so that the Identity Source is created.
Configuring Active Directory Identity Source for use with SSO 6.0
1.Log in to the vSphere Web Client as administrator@vsphere.local or as another user with SSO administrator privileges.
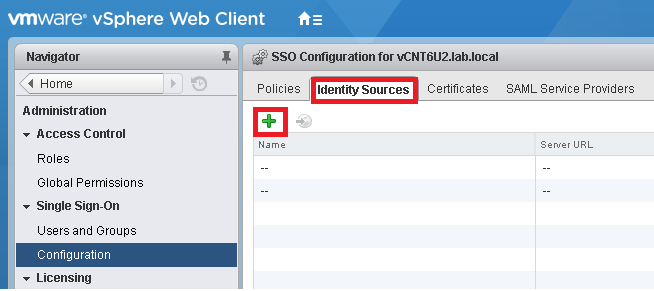
2.Navigate to Administration > Single Sign-On > Configuration. 
3.In the Identity Sources tab, click the Add Identity Source icon under the option menu.
4.Click Active Directory (Integrated Windows Authentication).
5.Select the Use SPN option.
6.Enter these information:
Domain name: DNS_Domain_name
Service Principal Name (SPN): STS/DNS_Domain_name
User Principal Name (UPN): Domain User assigned SPN@DNS_Domain_name.com
Password: Password
For example:
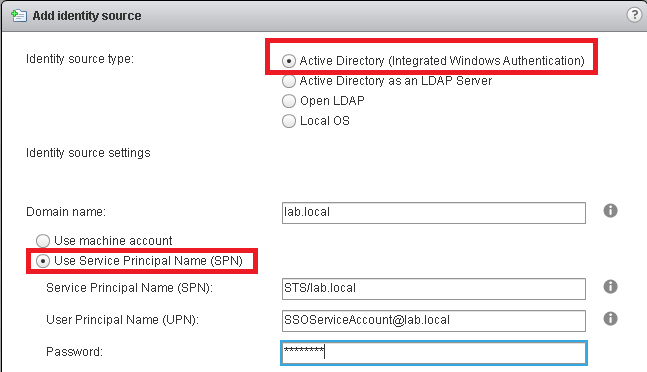
Domain name: lab.local
Service Principal Name (SPN): STS/lab.local
User Principal Name (UPN): SSOServiceAccount@lab.local
Password: Achieve@2016